This is the first in a three-part series on software and security in the cloud.
For the last 30 years, most organizations have used the same model for managing computers and software. There was a central computer or network server in the building with workstations attached. Depending on the application, data was usually on the server while programs were on the workstation. As software and servers grew larger and faster, more and more programs and information were stored on the server. It made things easier to maintain and update.
Then along came this thing called the cloud. Stripped of all the jargon, the cloud is simply a different place to store your programs and data. A hosting facility provides the use of servers that store your programs and you use an internet connection to access them. You can do this from the office, your home and anywhere you have an internet connection.
But there are different kinds of connections. Public websites, like CNN, local newspapers and other sites that don’t deal with sensitive information, do not concern themselves with security. Other sites such as your bank operate on a secured connection. Most shopping sites are a hybrid of non-secure (so you can see the goods for sale) and secure (so that it is safe to give them your credit card number). OpenRDA 4.0, when hosted in the cloud, will make use of secured server connection.
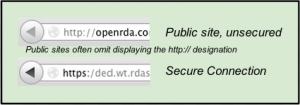 What a secure connection provides is the encryption of your data before it is sent from one site to another. Encryption technology “salts” your data with additional characters that makes the data incredibly difficult to read. An encryption key is used to return the data to its original state. This is the most popular method of providing cloud security. You know you are on a secure connection when the address of a site starts with “https” rather than “http”.
What a secure connection provides is the encryption of your data before it is sent from one site to another. Encryption technology “salts” your data with additional characters that makes the data incredibly difficult to read. An encryption key is used to return the data to its original state. This is the most popular method of providing cloud security. You know you are on a secure connection when the address of a site starts with “https” rather than “http”.
Most cloud software has become “browser-centric” and OpenRDA 4.0 is as well. This means it uses the standard browser features you are used to using for the regular internet access. Browser-centric software can:
-
Be easier to learn and use because of the familiar browser look and feel
-
Take advantage of printers and other shared network tools without additional setup
-
Have more choices in workstations and mobile devices
-
Make use of the browser security features to help keep your data secure
Browser providers are extremely concerned about security and spend a lot of time, effort, and money to protect your information. A recently released study found Firefox to be the most secure browser. Although this is subject to change from time to time as the different vendors continue to work on security issues, we recommend Firefox, both for the security and the functionality.
Next post we will cover what types of security measures you should expect from your hosting, whether it is in the cloud or internal. If you have any questions please leave a comment or give us a call.





